 in the toolbar and then select Configuration > Active Directory / LDAP. The Active Directory / LDAP Settings screen displays showing the current Active Directory / LDAP settings.
in the toolbar and then select Configuration > Active Directory / LDAP. The Active Directory / LDAP Settings screen displays showing the current Active Directory / LDAP settings.| Notes: l | The StorCycle solution uses the domains configured on the server, including multiple domains, to access a DNS (Domain Name System) to resolve UNC (Universal Naming Convention) paths over the domain and uses Active Directory / LDAP to verify restore users are valid on the domain. |
| l | StorCycle does not support anonymous requests to Active Directory / LDAP. In order to receive e-mail updates, users must have valid Active Directory / LDAP credentials. |
If desired, use the instructions below to configure Active Directory / LDAP.
| 1. | Click Settings  in the toolbar and then select Configuration > Active Directory / LDAP. The Active Directory / LDAP Settings screen displays showing the current Active Directory / LDAP settings. in the toolbar and then select Configuration > Active Directory / LDAP. The Active Directory / LDAP Settings screen displays showing the current Active Directory / LDAP settings. |
|
|
|
Figure 53 The Active Directory / LDAP Settings screen. |
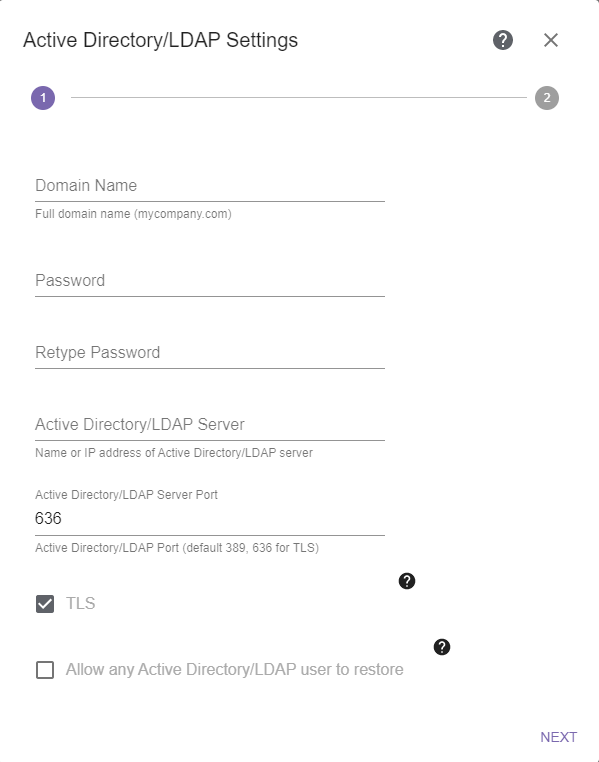
| 2. | Click Configure Active Directory / LDAP. The Active Directory / LDAP Settings dialog box displays. |
|
|
Figure 54 The Active Directory / LDAP Settings dialog box screen 1. |
| 3. | Enter the Active Directory Domain Name in the format Domain.com. |
| 4. | Enter and retype the Password for a user authorized to make Active Directory / LDAP queries. |
| 5. | Enter the IP address or hostname for the Active Directory / LDAP Server. |
| 6. | If desired, modify the Active Directory / LDAP Server Port to connect to the Active Directory server. |
| 7. | Select or clear the TLS check box. If selected, the StorCycle solution uses secure SSL/TLS to connect to the server. Spectra Logic recommends enabling SSL/TLS. The StorCycle solution supports TLS 1.0, 1.1, and 1.2. |
| 8. | Select or clear Allow any Active Directory / LDAP user to restore. If selected, any Active Directory / LDAP user on the domain can restore files even if they are not configured as a StorCycle user. These users can only restore files using an HTML link. |
| Note: | Restore only Active Directory / LDAP users count against the licensed user limit. |
| 9. | If you selected Allow any Active Directory / LDAP user to restore, select whether to Limit Daily Restores to limit the amount of data an AD / LDAP user can restore each day and if selected, enter the Daily Restore Limit. The daily limit is from midnight to midnight UTC. |
|
|
|
Figure 55 The Active Directory / LDAP Settings dialog box with Allow any Active Directory / LDAP user to restore selected. |
| 10. | Click Next. The second screen of the Active Directory / LDAP Settings dialog displays. |
|
|
|
Figure 56 The Active Directory / LDAP Settings dialog box screen 2 without Use OpenLDAP selected. |
| 11. | Select whether or not to Use OpenLDAP. If you select Use OpenLDAP, continue with Configure Active Directory / LDAP Using OpenLDAP. If you do not select to use OpenLDAP, continue to Step 12. |
| 12. | Enter a User, in the format user@domain, for the user associated with the passwords on the previous screen. The user must be authorized to make Active Directory / LDAP queries. |
| 13. | If desired, enter a custom User / Group Membership Query. |
|
IMPORTANT |
Only system administrators who have an understanding of the organizations domain settings should modify the AD/LDAP group search query. |
| 14. | Click Submit to save the Active Directory / LDAP settings. |
If you selected Use OpenLDAP, the dialog box updates to display the OpenLDAP setting fields.
|
|
|
Figure 57 The Active Directory / LDAP Settings dialog box with Use OpenLDAP selected. |
| 1. | Enter the BindDN, for example cn=admin, dc=example, dc=com. This is the credential used to authenticate to the LDAP server and perform operations. |
| 2. | Enter the BaseDN, for example cn=people, dc=example, dc=com. This specifies the root location for the LDAP search for user accounts. |
| 3. | Enter the Username Attribute, for example a UID, for the user associated with the passwords on the previous screen. The user must be authorized to make Active Directory / LDAP queries. |
| 4. | Enter the Email Attribute, for example mail. |
| 5. | If desired, enter a custom User/Group Membership Query. |
|
IMPORTANT |
Only system administrators who have an understanding of the organizations domain settings should modify the AD/LDAP group search query. |
| 6. | Click Submit to save the Active Directory / LDAP settings. |